In the world of the internet, every industry has its presence in the digital world. So to protect data from cyber-attacks it’s very important to understand what computer security is along with computer security types, and attacks and most importantly how can one take computer security as a career.
The Internet is one of the best things that has changed the world in many good ways. As we know that there is always another side to the coin. Similarly, security threats come due to the vast network and its technologies. Therefore, this raises the question of what computer security is in today’s time and how can we protect our system from known and unknown threats outside the internet world. Certainly, the demand for a career in computer security is increasing nowadays. So, let’s understand in detail what is computer security before understanding types, and cyber-attacks and then how I can make a career in computer security.
Why computer security is important?
Computer security is also known by the name cyber security or information technology. To clarify the computer security definition says that it is the practice of protecting computer systems and networks from digital attacks, theft and damage. The computer security definition looks easy to understand but it involves a wide range of measures and technologies designed to prevent these kinds of attacks which involve unauthorized access to computer systems, data, and networks and to protect against threats such as malware, ransomware, and phishing attacks.
Above all along with the computer security definition, one should know the importance of computer security. if we dont take the proper measures, in terms of cyber security or computer security sensitive information can be stolen or accessed by cybercriminals. Eventually, it can result in losses in many ways, such as financial losses, reputational damage, and many other consequences for organizations and individuals. So as the demand for the internet is increasing day by day, the need for the proper security system is also increasing.
Types of Computer Security Attacks
However, most people get wondered what is computer security has to do with my computer. what are all different types of computer security attacks? Why does our system get hacked .In other words we can say why our information gets stolen? So let’s understand computer security attacks first. There are many types of computer security attacks. Firstly ,One should understand the types of attack before learning what categories comes under computer security type. To mention few of the cyber security attacks are
1. Malware Attack

The most common attack out of many computer security attacks is Malware. These types of attacks involve using malicious software to compromise a computer’s or network’s security. Furthermore, the malware also has different types like
a)Viruses
These are programs that replicate themselves by attaching to other files and spreading to other computers. Hence, they can cause a variety of problems, including deleting files, stealing personal information, and displaying unwanted ads.
b)Worms
These are similar to viruses, but they can spread on their own without attaching to other files. They can exploit vulnerabilities in a system to replicate and spread to other computers.
c)Trojans
These are programs that appear legitimate but are malicious. They can be used to gain unauthorized access to a system or steal sensitive information.
d)Ransomware
Similarly Ransomware are Malware which encrypts a victim’s files and in return attackers demand a ransom from the victim to restore access.
2. Phishing attacks

The next name which comes under the types of computer security attacks is Phishing attacks. These are attempts to trick users into revealing sensitive information, such as passwords or credit card numbers, by posing as a legitimate entity in an electronic communication. This can be done via email, social media, or other online platforms.
3. Password Attack

Password attack is one of the most common types of computer security attacks nowadays. These attacks involve attempting to guess or obtain passwords to gain unauthorized access to a system.
There are many different methods for doing this, including using a list of common passwords, trying to reset the password through social engineering, or using a program to try multiple passwords in quick succession (a “password brute-force attack”).
4. Man-in-the-middle attacks
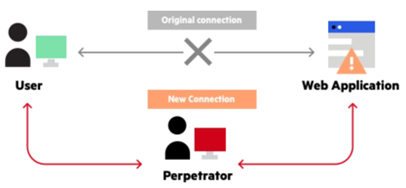
Man-in-the-middle attacks category of computer security attacks means intercepting or listening to communication between two parties without permission. This means first stealing information and then modifying it. This can be done by positioning themselves between the two parties and intercepting their traffic, or by compromising one of the parties and using it to relay messages. This is to say that this kind of attack is used to steal information on a credit card, login passwords, or account details.
An attacker can use this information in doing frauds related to finance, identity theft and many more.
5. SQL injection attacks

SQL attacks are one of the many computer security attacks. These attack means injecting malicious code into a website’s database. This is done via a vulnerable input field, such as a search bar. This kind of attack can lead to unauthorized access to very sensitive or secret data. The injected code can then be used to access or modify the database, potentially leading to the theft of sensitive information.
6. Denial of service (DoS) attacks
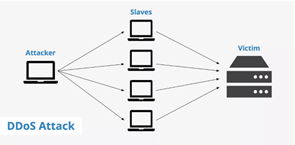
Another type of computer security attack is a Denial of service (DoS) attack. DoS attacks are done by flooding a website or network with traffic so that it becomes unavailable to users. This can be done using a network of compromised computers (a botnet) to generate the traffic, or by using a single device to send a high volume of requests. In short, this type of attack shut down the computer system or network and makes it unavailable or inaccessible for users. There are generally two types of DoS attac
- Application Layer Attack
- Network Layer Attack
7.Cross-site scripting (XSS) attacks
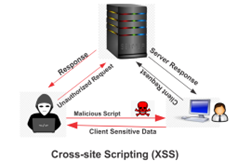
Cross-site Scripting is another but not the last type of cyber security attack. These involve injecting malicious code into a website that is then executed by other users’ browsers. In this type of attack, attackers inject executable scripts but malicious ones into the code of the trusted website. Usually, they initiate this attack by sending malicious links. XSS type of attacks can be used to steal sensitive information.
After understanding what is computer security and why computer security is important let’s get knowledge on what all types of computer security attacks are there. Now let’s know what all computer security types are available.
Computer Security types
1. Network security
After understanding what is computer security one should know about all computer security types. Among many securities types network security is one of the most commonly used by people. It refers to the practices and technologies that are used to protect a computer network and its associated devices. Also, data is transmitted by using unauthorized access. Network security is important because it helps to ensure the confidentiality, integrity, and availability of the data and resources on a network.
To clarify, network security there are different methods and technologies like:
a)Firewalls
These are software programs which control incoming network traffic and outgoing network traffic depending on predetermined security rules.
b)Virtual private networks (VPNs)
These are networks that use encryption to secure data transmitted over the internet.
c)Intrusion detection and prevention systems (IDPS)
These are systems that monitor network traffic and alert administrators to potential security threats.
d)Encryption
This is the practice of encoding data to make it unreadable to anyone who does not have the proper decryption key.
e)Access control
The access control method means placing control for networks which mentions who has access to that network.
f)Network segmentation
This involves dividing a network into smaller subnetworks, or segments, to limit the scope of an attack
g)Patch management
This involves regularly installing updates and patches to fix known software and operating systems vulnerabilities.
In network security, there are many methods and technologies. Hence,it is important for organizations to regularly assess their security needs and implement appropriate measures to protect their networks and data.
2. Internet security

Another name in computer security types is internet Security. Internet security refers to the measures taken to protect devices, networks, and online systems from threats that originate on the internet.
Internet security is important for individuals and organizations, as it helps to protect against cyber-attacks that can result in financial loss, reputational damage, and other consequences. It’s important to use strong passwords, keep software and security measures up to date, and be cautious when clicking on links or downloading files from the internet in order to stay safe online.
3. Endpoint security

The next category in computer security types is endpoint security. This security protects those devices which connect to the network. For example, mobile phones, computer systems, and tablets. This endpoint security is an evolved version of antivirus software that can protect computer systems from sophisticated malware attacks also. Ultimately leading to no threat day for users. It helps in preventing the breeching of sensitive data and other cyber-attacks.
4. Application Security

Application security is one of the many computer security types where it practices building and maintaining secure applications that can protect against various cyber threats. For example, hacking and data breaches. This includes measures taken during the development and testing of applications and after they have been deployed.
Overall, application security is an important aspect of cybersecurity and is essential for protecting against a wide range of threats. By following best practices and implementing appropriate security measures, organizations can help to ensure the security and integrity of their applications.
5. Data security

Data security means the protection of data from unauthorized access and protecting the use, disclosure, or destruction of data. It involves the use of various technologies, processes, and controls to secure data and prevent unauthorized access or misuse. Professionals with proper knowledge of data security can implement this properly.in return, they can protect the organisation’s data assets from digital thefts by using robotics strategies.
6. Cloud security

Cloud security is the practice of protecting data and applications that are stored in the cloud from unauthorized access, use, disclosure, disruption, modification, or destruction. It involves a range of measures and controls that are implemented to ensure the confidentiality, integrity, and availability of cloud-based resources. Irrespective of the industry every company that is transforming itself towards the digital world needs cloud security to protect its sensitive data. Cloud security is an important part of computer security in today’s world where digital threats are increasing day by day.
7. Mobile Security

Mobile security refers to the protection of mobile devices, such as smartphones and tablets, from various cyber threats. With the increasing use of mobile devices for personal and business purposes, mobile security has become a critical concern for individuals and organizations.
There are several key components to effective mobile security:
a)Mobile device management (MDM)
MDM solutions can be used to enforce security policies on mobile devices and ensure that they are compliant with an organization’s security standards.
b)Mobile antivirus software
This helps to protect mobile devices against malware, such as viruses, worms, and Trojans.
c)Encryption
Encrypting data transmitted between mobile devices and the network helps to protect against eavesdropping and other types of cyber-attacks.
d)Security updates
It’s important to keep mobile devices up-to-date with the latest security patches and updates to help protect against the latest threats.
e)User education
Education for mobile security is provided to users. It includes the importance of mobile security and best practice to protect their mobiles.
Overall, mobile security is an essential component of a comprehensive cybersecurity strategy. By implementing appropriate security measures and following best practices, individuals and organizations can help to ensure the security and integrity of their mobile devices.
8. Email security

Email security refers to the protection of email communications from various cyber threats, such as spam, phishing attacks, and malware. It involves the use of various technologies, processes, and controls to secure email and prevent unauthorized access or misuse.
There are several key components to effective email security:
a)Spam filters
This help to identify and block unwanted or malicious emails from reaching users inboxes
b)Encrypted Email
Moreover here in this category of email security, email encryption protects the emails from unauthorised access. They protect messages by allotting a decryption key to messages. People with these keys only have access to read emails
c)Authenticated Emails
This involves verifying the identity of the sender of an email to help ensure that it is not a fake or spoofed message.
d)Email archiving
Email Archiving means archiving messages so that it can ensure that messages are preserved properly. In addition, we can retrieve back these messages whenever we need them.
e)User education
This component of email security includes the education of users. In other words, we can say that users get knowledge about email security and what are the best practices for protecting themselves against email-based threats.
9. Physical security

Likewise, another category under computer security systems is physical security. In short, it means physical assets like data centres or servers are protected from unauthorised access. In other words, we can say prevent the system from getting tempered.
A career in computer security

Till now we have a clear understanding that the computer security career is a very promising path .Undoubetly who has clear and detailed knowledge of what is computer security, what are computer security types and what all are computer security attacks can perform very well in this line. Subsequently, there are many opportunities in the market if someone wants to enter into the computer security or cyber security field.
1. Cybersecurity Specialist
The first name in the computer security career path is cybersecurity specialist. For this role or profile, one should have strong IT skills along with the ability to give attention to minute details. One should have good knowledge of identifying the strength and weaknesses of IT systems. On average cyber security specialists can get a salary of Rs.11,31,000 per annum in India.
2. Cyber Crime Analyst
Then comes the designation as a cybercrime analyst when it comes to knowing about computer security careers. The most important skills required for this role are scripting, Hacking, and Networking along with good knowledge of the operating system.
3. Incident Response Analyst
Incident Response analyst is another path for a cyber security career. The skills required for this area are technical writing and documentation. Candidate should be able to give attention to detail along with intrusion detection of tools. In addition to this candidate should have good knowledge of forensic software.
4.Risk Analyst
Another field in the cyber security career path is the role of risk analyst. However, the Skills required to enter into this role are Risk Management, Procedures, and Data Analysis along with knowledge of risk Assessments and Regulatory Agencies.
A career in computer security can be very rewarding and it is an in-demand field with a lot of opportunities.
To enter a career in cyber security, you may need to earn a degree in a related field, such as computer science or information technology. Some employers may also require you to have a professional certification, such as the Certified Information Systems Security Professional (CISSP) or the Certified Ethical Hacker (CEH). Furthermore, You can go for professional courses in the field of cyber security by institutes like Henry Harvin.
Conclusion
In conclusion, everyone is in the digital world today which in turn increases the risk of becoming the victim of cyber-attacks. So, it becomes very important to understand what is computer security even a common person should understand also. When we understand what is computer security than only, we can take steps to protect it. Computer security is a very promising and lucrative line of career path to enter. Doing courses related to cyber security can make you land high-paying jobs.
Frequently Asked Questions
Ans- Computer security is the protection of computer systems and networks from the theft of or damage to the hardware, software, or information on them.
Ans- Computer security is important because it helps to protect the confidentiality, integrity, and availability of data and systems. Without effective cyber security, an organization’s sensitive information and systems could be compromised, leading to financial loss, legal liabilities, and damage to reputation.
Ans- Some common threats to cyber security include viruses, malware, ransomware, phishing attacks, and hacking. Other threats include physical damage to computer systems, unauthorized access to systems and data, and denial of service attacks
Ans- There are many courses to enter into cyber security. However, cyber security academy of many institutes offers certified cyber security courses. These are short-duration courses and can be done along with present job.
Ans- On Average salary hike is of 80%. Moreover, it depends on the person’s overall knowledge and profile also.








![Harvin Harvin Education Reviews: 2023 [Updated]](https://bestcoursenews.com/wp-content/uploads/2023/01/download-28-100x70.jpeg)


